Why Cryptography is the Backbone of Blockchain
Blockchain technology is often described as “trustless” yet “secure.” But what actually makes it so? The answer lies in cryptography, the invisible layer of mathematics and algorithms that underpins every blockchain transaction. Without cryptography, digital assets like cryptocurrencies, smart contracts, and decentralized applications would be vulnerable to tampering and fraud.
Cryptography in blockchain security ensures that transactions are verifiable, data integrity is maintained, and user identities are authenticated—all without relying on a central authority. From hashing and digital signatures to advanced privacy-preserving methods like zero-knowledge proofs, cryptography enables trust in a decentralized world.
As blockchain adoption accelerates across finance, healthcare, supply chain, and government sectors, understanding its cryptographic foundation becomes crucial—not just for developers but also for businesses, investors, and regulators.
What is Cryptography in Blockchain?
At its core, cryptography is the practice of securing information through mathematical techniques. In blockchain, it serves three main purposes:
- Data Integrity: Ensuring that once a transaction is recorded, it cannot be altered.
- Authentication: Verifying that transactions come from legitimate users.
- Privacy: Protecting sensitive information from unauthorized access.
Unlike traditional IT systems, blockchain relies on a decentralized structure. Cryptography replaces the need for a central authority by making tampering virtually impossible. By securing each block and linking it to the previous one, blockchain forms a tamper-proof ledger—a foundational principle for cryptocurrencies, smart contracts, and decentralized applications.
Why is Cryptography Important for Blockchain Security?
Imagine a world where digital transactions could be altered or reversed without anyone noticing. That’s the nightmare scenario cryptography prevents. Here’s why it’s essential:
- Trust Without Central Authority: Blockchain operates without banks or intermediaries. Cryptography ensures participants can trust the system itself.
- Privacy and Security: Digital signatures, hashing, and encryption protect both user identities and transaction details.
- Preventing Fraud: By making tampering computationally infeasible, cryptography stops double-spending and data manipulation.
Real-world applications prove this: Bitcoin and Ethereum use cryptographic algorithms to secure billions of dollars in transactions daily, while enterprises increasingly rely on blockchain for supply chain and contract management.
Key Cryptographic Techniques in Blockchain
Blockchain security depends on several cryptographic techniques:
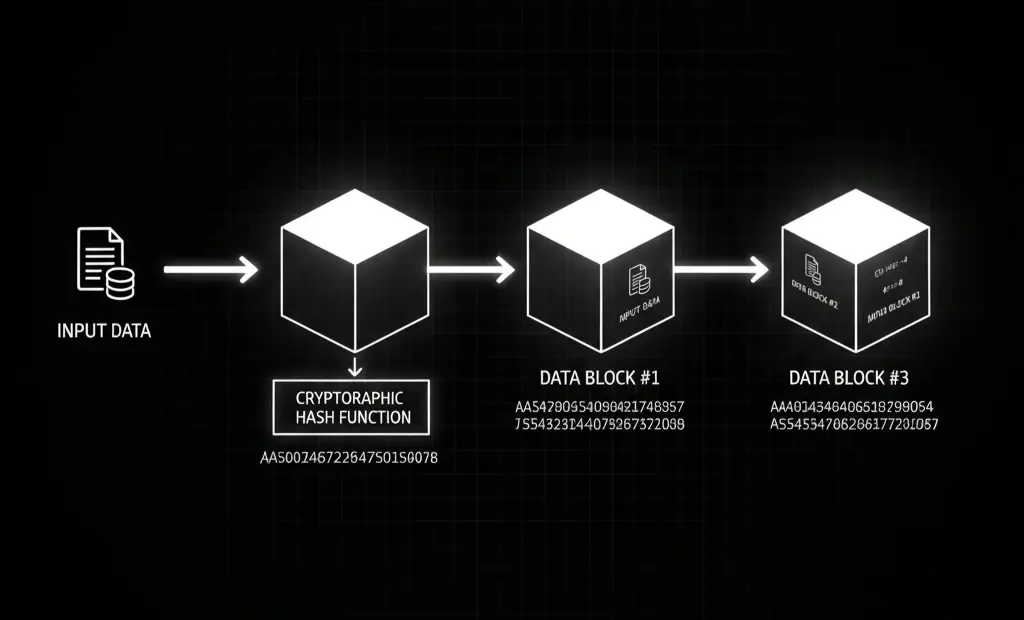
1. Hash Functions
Hashing converts data into a fixed-length string of characters. Each block contains a hash of the previous block, making any tampering immediately obvious. SHA-256 and Keccak are common algorithms.
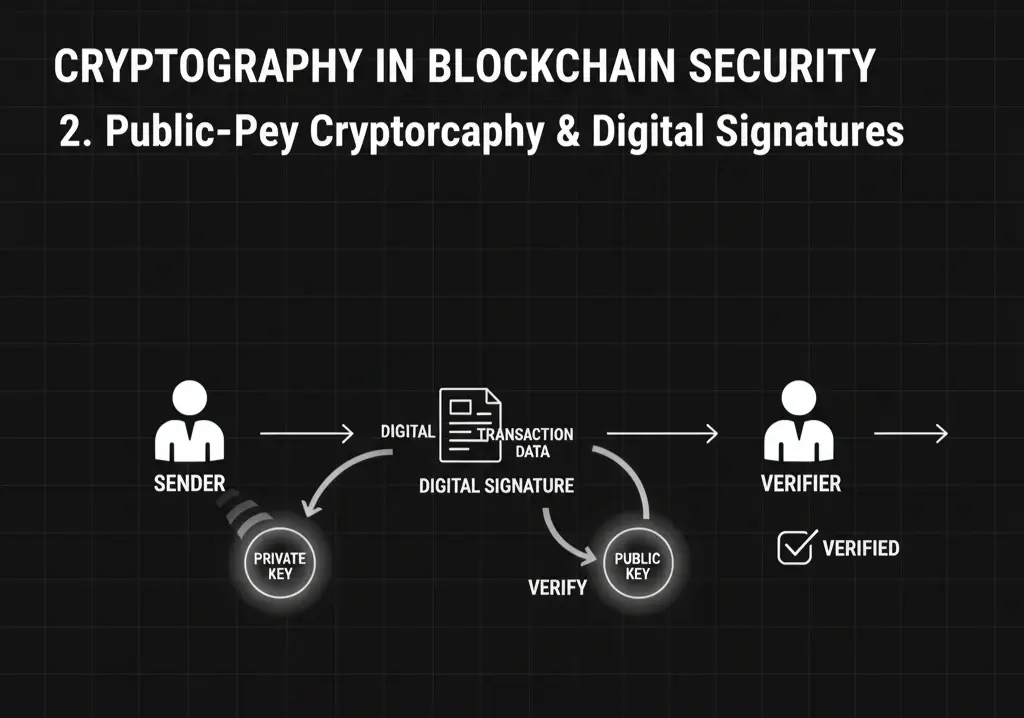
2. Public-Private Key Cryptography (Asymmetric Encryption)
Users have a private key (secret) and a public key (shared). Transactions are signed with private keys and verified with public keys, ensuring only rightful owners can initiate transactions.
3. Digital Signatures
Digital signatures authenticate the sender of a transaction. Algorithms like ECDSA or EdDSA ensure that the signature is unique and verifiable, preventing impersonation.
4. Zero-Knowledge Proofs (ZKPs)
ZKPs allow one party to prove knowledge of a secret without revealing it. This enhances privacy in blockchain transactions while maintaining trust.
Together, these techniques make blockchain secure, transparent, and decentralized.
How Cryptography Protects Blockchain Transactions
Hashing and digital signatures work together to secure blockchain transactions:
- Hashing locks the contents of a block, linking it to the previous block and creating a chain that is tamper-resistant.
- Digital signatures verify that the sender is authorized and that the transaction is authentic.
- Public-private key cryptography ensures that only intended recipients can access sensitive data.
These mechanisms make it nearly impossible to alter a blockchain without detection, even in a decentralized network with thousands of nodes.
Can Blockchain Be Hacked Despite Cryptography?
While cryptography is robust, blockchain is not entirely invulnerable. Potential threats include:
- 51% Attacks: If a single party controls the majority of the network’s computing power, they could manipulate transactions.
- Key Theft: Stolen private keys can give attackers access to funds.
- Phishing Attacks: Users tricked into revealing keys or passwords compromise security.
- Smart Contract Vulnerabilities: Bugs in code can be exploited even if the underlying blockchain is secure.
Cryptography provides strong protection, but user behavior, network design, and code quality also play critical roles in security.
Challenges and Limitations of Cryptography in Blockchain
Despite its strengths, cryptography faces challenges:
- Quantum Computing Threats: Future quantum computers could break current encryption algorithms.
- Scalability Issues: Advanced cryptography can require significant computational resources.
- Key Management Risks: Losing a private key can mean permanent loss of assets.
- Complexity for Users: Non-technical users may struggle to manage keys and understand cryptographic principles.
These challenges highlight the need for continued innovation and education in cryptographic methods.
Future of Cryptography in Blockchain Security
The future is exciting and evolving:
- Post-Quantum Cryptography: Algorithms resistant to quantum computing will safeguard future blockchains.
- Advanced Zero-Knowledge Proofs: Privacy-preserving techniques will become faster and more scalable.
- Homomorphic Encryption: Enables computations on encrypted data without revealing it, enhancing security and privacy.
- Regulatory Standards: Governments and industry bodies are likely to define stricter security requirements.
Cryptography will continue to evolve, ensuring that blockchain remains a secure foundation for digital trust in the coming decade.
How Organizations Can Benefit
Understanding and adopting cryptography best practices benefits businesses and developers:
- Secure Digital Assets: Protect cryptocurrencies, tokens, and smart contracts from fraud.
- Build Trust: Demonstrate reliability and transparency to customers and partners.
- Mitigate Risks: Proactively address security threats and regulatory compliance.
- Stay Ahead of Technology: Implement innovations like zero-knowledge proofs and post-quantum cryptography early.
Even small enterprises can leverage cryptography effectively by choosing the right blockchain platform, educating users, and implementing secure key management.
FAQs (People Also Ask)
Q1: What is the difference between symmetric and asymmetric cryptography in blockchain?
Symmetric uses a single key for encryption and decryption, while asymmetric uses a public-private key pair. Blockchain relies on asymmetric methods for transaction authentication.
Q2: How do cryptographic hash functions contribute to immutability?
Hashes create a unique fingerprint for each block. Any change alters the hash, breaking the chain and immediately revealing tampering.
Q3: What are zero-knowledge proofs?
They allow users to prove they know information without revealing the actual data, enhancing privacy in blockchain transactions.
Q4: How vulnerable is blockchain to quantum computing attacks?
Current cryptography could be broken by future quantum computers, prompting research into post-quantum algorithms.
Q5: How should private keys be managed?
Keys should be stored securely offline, backed up, and never shared to prevent theft and loss of assets.
