
Introduction: My Journey Into the World of Encryption
Not too long ago, I was preparing to send a confidential financial report to a partner overseas. I remember staring at my laptop thinking: “What if someone intercepts this? How can I be sure it stays safe?”
That’s when I dove deep into encryption, and I realized there’s more than one way to lock up your digital secrets. Specifically, there are two main types—symmetric and asymmetric encryption.
I want to share with you what I learned—not as a textbook, but as a story of how I understood and used these tools in real life. By the end, you’ll know not just the differences, but also how to use them wisely.
Symmetric Encryption: One Key to Rule Them All
I like to think of symmetric encryption as sharing a secret key between me and a friend. Imagine we have a box and the same key to lock and unlock it. Whatever I put in that box, you can open with the same key.
- Single key: Same key for encryption and decryption
- Super fast: Can encrypt large files quickly
- Main risk: How do we share the key safely?
I remember once sending a password over email to a colleague. My stomach sank thinking, “If anyone else reads this, they have access too!” That’s the main downside of symmetric encryption—the key itself must be protected at all times.
Popular Algorithms: AES, DES, 3DES, and ChaCha20.
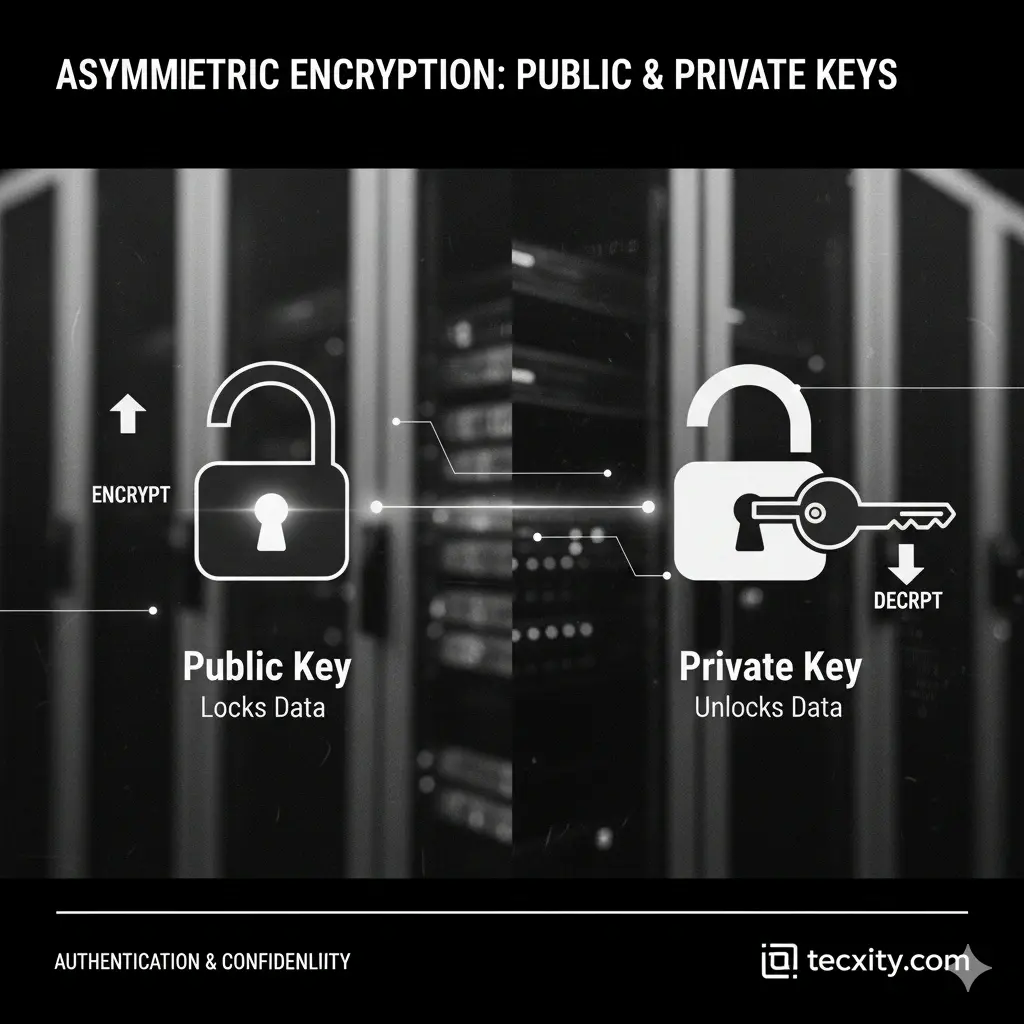
Asymmetric Encryption: The Magic of Two Keys
Asymmetric encryption felt like magic when I first learned it. Instead of one key, it uses two keys:
- Public Key: Anyone can know it
- Private Key: Only you hold it
Think of it like a mailbox on your street: anyone can drop letters into it (public), but only you have the key to open it (private).
- Solves the “key sharing” problem
- Slower than symmetric encryption
- Ideal for digital signatures and secure communications
Popular Algorithms: RSA, ECC, and Diffie-Hellman.
Symmetric vs Asymmetric: A Quick Comparison
To keep things simple, I made a table that helped me understand the differences quickly:
| Feature | Symmetric Encryption | Asymmetric Encryption |
| Keys Used | One key (shared) | Two keys (public + private) |
| Speed | Very fast | Slower |
| Security Risk | Must share key secretly | Public key can be shared openly |
| Best For | Large files, databases, VPNs | Secure communication, digital signatures |
| Example Algorithms | AES, DES, ChaCha20 | RSA, ECC, DSA |
Why We Often Use Both: The Hybrid Model
Here’s where it gets really clever. In real life, we usually use both types together.
Take HTTPS, the protocol that secures every website you visit.
- Asymmetric encryption is used to safely exchange a secret key.
- Symmetric encryption takes over to encrypt the data itself.
I like to think of it this way: asymmetric encryption is the handshake, and symmetric encryption is the conversation.
Real-Life Examples You’ve Probably Encountered
Once I started paying attention, I realized encryption is everywhere:
- Online Shopping: HTTPS uses asymmetric for key exchange, symmetric for speed
- Emails: PGP ensures only the intended recipient can read your message
- File Storage: Zipping files with a password uses symmetric encryption
- VPNs: Rely on symmetric algorithms like AES for bulk data encryption
- Digital Signatures: Asymmetric encryption verifies software downloads
Every day, our data is protected without us even noticing.
Speed and Performance: Why It Matters
One thing that surprised me is the speed difference:
- Symmetric (AES) can encrypt gigabytes of data in seconds
- Asymmetric (RSA) is much slower due to complex math
That’s why asymmetric encryption is rarely used to encrypt entire files—it’s too slow. Instead, it exchanges a tiny secret key, and symmetric encryption does the heavy lifting.
Real-World Challenges and My Takeaways
Even with encryption, nothing is perfect. Here’s what I learned:
1. Quantum Computing Threats
Quantum computers could break current asymmetric algorithms like RSA. Researchers are already developing post-quantum encryption to stay ahead.
2. Key Management
The biggest weak point is human error. Losing private keys, reusing passwords, or misconfiguring systems can compromise everything.
3. Performance Trade-Offs
Asymmetric encryption is great for small messages, but it’s not practical for huge datasets without combining it with symmetric encryption.
4. Side-Channel Attacks
Hackers sometimes exploit how encryption is implemented, rather than the math itself. Timing attacks or monitoring power usage can reveal secrets if not protected.
FAQs: What I Often Get Asked
Q1: Which is safer symmetric or asymmetric?
Both are secure when implemented correctly. Symmetric is faster; asymmetric is more flexible. Together, they’re unbeatable.
Q2: Can I use symmetric encryption for huge files?
Absolutely. That’s its main strength—speed and efficiency.
Q3: Why not just use asymmetric encryption everywhere?
It’s slower and uses more resources. You don’t want Netflix buffering because your encryption is struggling!
Q4: Is quantum computing a threat right now?
Not today, but in the near future, yes. Post-quantum cryptography is becoming a hot topic.
Q5: Can small businesses use encryption?
Yes! Many SaaS platforms offer hybrid encryption solutions for emails, cloud storage, and digital identity management.
Conclusion: Why You Should Care
Encryption might seem technical, but it affects all of us every day.
- Symmetric encryption gives speed and efficiency
- Asymmetric encryption gives security and trust
- Hybrid encryption gives both, forming the backbone of secure communication online
The next time you see that little padlock in your browser, remember: there’s a dance happening between symmetric and asymmetric encryption to protect you and me.
If I hadn’t learned this, I would still be sending sensitive files across the internet with a lingering fear of interception. Now, I feel confident knowing my data and yours is protected.
